This post is a one in the “Rethink Cybersecurity” series. Additional posts in this series are available here
Recognizing the industry interplay, DHS recently moved to a new model based on an industry determined function-based framework. Taking a functional view widens the lens to move closer to this interconnected, multi-industry reality. Under the leadership of the Cybersecurity
& Infrastructure Security Agency (CISA), has a comprehensive program to:
• Collect cyber incident data;
• Issue alerts, bulletins, frameworks, tips and tools; and
• Work with the private sector to assess and address critical cyber security risks.
Part of this program includes applying the risk management process to a list of “National Critical Functions” (NCFs). The functions represent services provided by “government and the private sector [that are] so vital to the United States that their disruption, corruption, or dysfunction would have a debilitating effect on security, national economic security, national public health or safety, or any combination thereof.” The NCFs include:
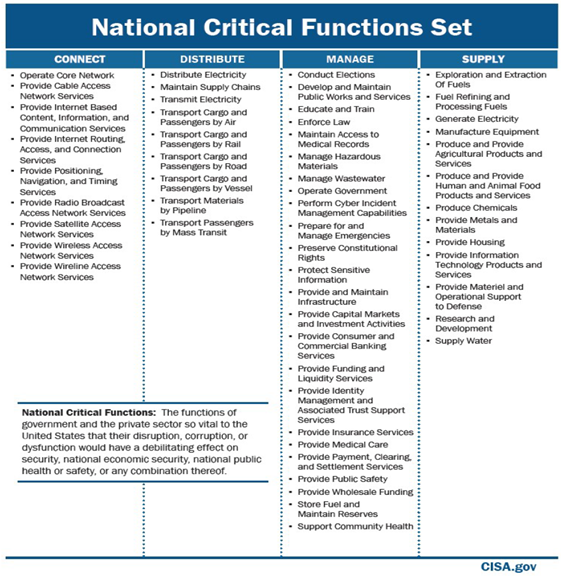
While this is an important step in the right direction his view is incomplete as multiple industries interact to deliver the same critical service. For example, the delivery of fuel requires activity across the energy, industrial manufacturing, technology, telecommunications, transportation and warehousing sectors.
NCFs, just like anybody else, will invariably rely upon common operating systems, widely used hardware and software and continuous high-fidelity bandwidth. NCFs will connect themselves – upstream and downstream – with counterparties that also rely on operating systems, hardware, software and bandwidth. There is a significant likelihood that one or more nodes in NCF networks will fail, potentially leading to property damage or loss of life. To achieve a full understanding of the “fabric of the world,” it will be necessary to evolve the National Critical Functions to a set of end-to-end “maps” of critical systems. To illustrate, we’ll look at one example – the availability of fuel at gas stations across the U.S. Many different actors are involved from the point of finding crude oil in the ground to pushing the button on the gas pump at the corner gas station. The American Petroleum Industry maps the oil supply chain as
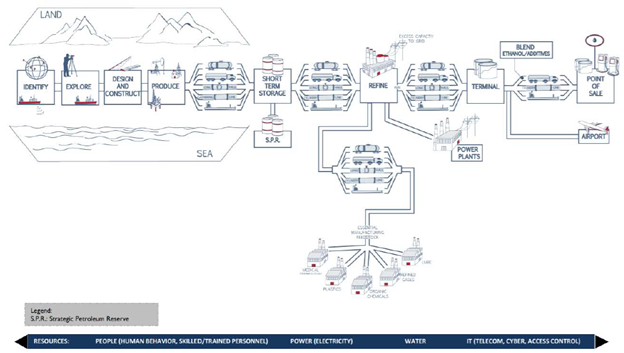
Each of the squares and connecting lines has a technology infrastructure and ecosystem – including hardware, software and vendors – supporting it. To properly assess the risk of disruption at the gas pump, we must work backward, map the strands in the fabric and zoom in on each thread. Some threads will be steel-braid – having more secure systems and software.
Others will be weaker, relying on outdated operating systems, vulnerable software or unstable vendors. All will be at risk because the fabric is woven together – or as many commonly say: “the system is only as strong as the weakest link.” The next step will be focusing on the “connective tissue” – the links that join each sub-function together to arrive at a macro-function. Then, analysis can be performed on weak points in the system and prioritized for risk management action. Continued work is needed to accelerate understanding of and action on systemic cyber risk.
The Federal government is in a central position to organize this effort in collaboration with private industry and academia. It is well within the Federal remit of protecting the nation’s critical infrastructure and keeping citizens safe from economic, physical and health impacts of systemic cyber events.
Join the Rethink Cybersecurity Community click here