This post is a one in the “Rethink Cybersecurity” series. Additional posts in this series are available here
In the early blogs in this series we illustrated that one of the major reasons not made substantial progress in securing cyberspace over the past 30 years is that we have generally thought of cyber risk primarily in technical/operational terms, and largely ignored the economic causes for most cyber-attacks.
The evidence for the economic causes of most cyber-attacks is fairly blatant. Cybercrime is a 2 trillion dollar a year issue (going to 6 trillion by 2023 according the World Economic Forum). China, and many others have been stealing our valuable intellectual property for decades and the current Verizon Breech study shows over 90% of cyber-attacks have an economic motive. Technology is only HOW cyber-attacks occur. To solve the problem, we also need to address WHY the attacks occur and the reason is almost always economic.
Much like traditional entity cyber risk, systemic cyber risk is not at heart a technology problem – it is an economic problem. Systemic Cyber risk emanates from highly concentrated markets for technology products and services.
The truth of the matter is that we’ve built a network of highly interconnected and tightly coupled counterparties that rely on common technology products and services. Failures at a single critical point can lead to cascading effects across the entire system.
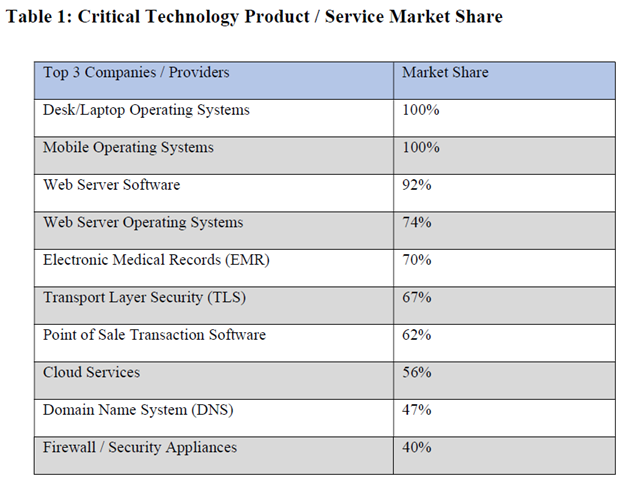
A rough market share statistic on critical technology products and services demonstrates how organizations throughout the U.S heavily depend on a few common services and products. In the U.S, the top three companies or providers are proving all the functioning desktop/laptop operating systems and mobile operating systems for businesses. Similarly, 92% of web server software are provided by the top three. The list goes on to demonstrate that most of the critical technologies depend on few number of vendors and if a product or service in these areas is flawed or fails, a widespread impact on the U.S businesses and economy seems inevitable.
Even without the statistics, this market phenomenon has been apparent with the rise of tech giants and how they have become part of our lives. Such market phenomenon, no doubt, has been well exploited by those with malicious intent, and it has been evident with most of the ransomware activities which brought heavy casualties. For instance, recent attacks include ransomware attacks on misconfigured Remote Desktop Protocol and exploiting vulnerabilities on commonly used Virtual Private Networks and Application Delivery controllers. The attackers are aware of the benefits of exploiting commonalities as they maximize their opportunities in achieving their goal – financial, competitive, or geopolitical.
Some of the recent ransomware attacks demonstrate how the failure of the central product or counterparty leads to widespread losses and cascading impact. In May of 2017, the infamous “WannaCry” ransomware attack infected hundreds of thousands of devices by exploiting a vulnerability in unpatched and unsupported versions of a commonly used operating system. The resulting economic loss was estimated to be between $4 -$8 billion. In June of the same year, the “NotPetya” attack spread throughout the globe. Similar to the WannaCry, NotPetya exploited unpatched vulnerabilities in an operating system, which brought business disruption and financial impacts. The estimated economic damage by NotPetya was over $10 billion. The common element, and the largest concern, is the reliance on a widely used software product or vendor. The number of these multi-party “ripple” events is increasing at an average annual growth rate of 20%, according to Cyentia Institute and RiskRecon report. Cyentia also estimates that the medial financial cost of ripple events is 13x larger than single-party incidents. As a society, there is much work to be done to address systemic risk. To do so, we should start by identifying the critical nodes of aggregation (NoAs). From there, we should assess NoAs to identify their vulnerabilities, provide adequate security procedures and policies to prevent them from being exploited by attackers. By taking the initiatives, we will take one step forward to ensure that our country will be prepared for threats attempting to exploit systemic risk.
Join the Rethink Cybersecurity Community click here